Deterministic
Algorithms vs. Chaos: The Weaponized Mathematics
of
Redemption’s Singularity, Bifurcation Points, and Bio-Hacking
by
Dallas F. Bell, Jr.
There
are only
two kinds of
men: the righteous who believe they are sinners, the sinners who
believe they are righteous.
Blaise
Pascal1
In
mathematics, the Sieve
of Eratosthenes,2
one of a number of prime
number sieves,
is a simple, ancient algorithm
for finding all prime
numbers up to any given limit. It does so by iteratively marking as
composite (i.e. not prime)
the multiples of each prime,
p, starting with the multiples of 2. Determining the distribution of
twin primes (p + 2 or prime numbers with a gap of two) involves
factorization algorithms in tandem with rotating symmetry groups.3
The prime spiral sieve generates symmetries in the form of
algorithmically permutated mapping matrices, palindromes, rotating
equilateral triangles, and complex polygons.4
Polynomial
time algorithms
are tractable. Any algorithm
with a time complexity that cannot be bounded by such bound is known
as non-polynomial
algorithms.
Deterministic, as opposed to probabilistic, accounts for 100% of
composite numbers within a given range, leaving only prime numbers,
and with 100% certainty.5
Arguably,
the most studied algorithm is the deterministic
algorithm. Given
a particular input, it will always produce the same output, with the
underlying machine always passing through the same sequence of
states.6
A non-deterministic
algorithm
is the execution of concurrent algorithms
with race conditions, which can exhibit different outputs on
different runs. Unlike a deterministic
algorithm
which travels a single path from input to output, a non-deterministic
algorithm
can take many paths, with some arriving at the same outputs, and
others arriving at different outputs. A deterministic
algorithm
that performs f
(n)
steps always finishes in f
(n)
steps and always returns the same result. A non-deterministic
algorithm
that has f
(n)
levels might not return the same result on different runs. A
non-deterministic
algorithm
may never finish due to the potentially infinite size of the fixed
height tree.7
Calculus
(Latin
for
a small
stone -
for counting) is used in many machine learning algorithms. The
subfield of calculus that cuts things into small pieces, differential
calculus, is concerned
with the study of the rates at which quantities change. It is one of
the two traditional divisions of calculus,
the other being integral calculus,
the study of the area beneath a curve.8
Simply put, a differential makes a difference between comparable
classes, such as with individuals and societal institutions, while
the calculus deals with the rate of change of functions with respect
to their variables: f
( )
and f
(
)
and f
( ).
In an email exchange with Dallas F. Bell Jr. during January, 2020,
Franco Vivaldi, professor of mathematics in the school of
mathematical sciences at the Queen Mary University of London,9
suggested that the mathematical symbol for algorithms, since most
algorithms are deterministic, be the function notation f
(x).10
).
In an email exchange with Dallas F. Bell Jr. during January, 2020,
Franco Vivaldi, professor of mathematics in the school of
mathematical sciences at the Queen Mary University of London,9
suggested that the mathematical symbol for algorithms, since most
algorithms are deterministic, be the function notation f
(x).10
All
life is observed operating in parameters from a beginning in a linear
succession of moments toward an end—an algorithm. A flower fades11
and a blade of grass soon dies, and ceases to have life.12
Their finite or temporal ending algorithm began out of infinite
creation process and can be expressed as
 (x).
All algorithms, f
(x),
have
a beginning point and thus finite origins but the end of some f,
humans and angels etc., may tend toward infinity13
and be generally expressed as
(x).
All algorithms, f
(x),
have
a beginning point and thus finite origins but the end of some f,
humans and angels etc., may tend toward infinity13
and be generally expressed as
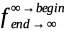 (x).
(x).
If
we consider numerical continuation, the algorithm purpose can be seen
by it being a predictor-corrector method. Deviations from truth can
be predicted and provide the opportunity to switch to the correct
vector. The parameter λ is a scalar and the solution u an
n-vector.14
Humans have then been purposefully created with bounds15
by a pre-existent infinite Intellect. That perfect Being must have
the non-material attributes of justice, love, and grace etc. As
such, He must have made available the Owner’s Manual of parameters
for individuals to efficiently operate in their vector space.
Historically, this is known as the Bible, which by necessity (logic
principle that infinite and therefore infallible author > finite
and therefore fallible readers) must have the supreme authoritative
attribute of sola
Scriptura.16
Considered a U.S. military genius17
selected as superintendent of the West Point Military Academy in
1852, the Christian General Robert E. Lee18
wrote the Bible is “a book in comparison with which all others in
my eyes are of minor importance: and which in all my perplexities has
never failed to give me light and strength.”19
He remarked at another time that “there are things in the old Book
which I may not be able to explain, but I fully accept it as the
infallible Word of God, and receive its teachings as inspired by the
Holy Spirit.”20
Global
(Dutch) architect, Remment Koolhaas observed in a 2020 television
interview that all people of the world like similar architectural
designs yet all people still show individual diversity of
preferences. The non-congruence of the choices of monozygotic twins,
raised together, commonly demonstrate human freewill. Choices may be
made by the freewill of intellects, humans and angels etc., and so
have bifurcation points, β, of congruence and non-congruence, with
the will of God the infinite Creator, and can be compared:
 and
and
 .21
For each bifurcation from untruth or truth, there is a branch of
solutions of the original problem which passes through the singular
point. That singularity of choice can be visualized as having a
radius, r.
In black holes, the singularity,
.21
For each bifurcation from untruth or truth, there is a branch of
solutions of the original problem which passes through the singular
point. That singularity of choice can be visualized as having a
radius, r.
In black holes, the singularity,
 ,
is reached when the radius equals 0, r
=
0, or is less than 0, r
<
0. Then the radius is less than the radius at the singularity, r
<
,
is reached when the radius equals 0, r
=
0, or is less than 0, r
<
0. Then the radius is less than the radius at the singularity, r
<
 .
When the metric radius of an object equals 0, r
=
0, the object may be considered infinite. So when r
=
0 it is a real singularity in certain coordinate systems.22
Obviously, having a radius means there is a fixed center (with
general coordinates of h and k) and an outer edge of the shape of
something. If all the radii are equidistant, the shape is a circle.23
The diameter, ⌀,
of that circle x 3.14… (lower case pi, 𝞹)
= the circumference of the circle, c. Inductively, c ÷ 𝞹
= ⌀,
which is 2 x r.
All finite entities project outwardly from their center point
(⊙A
represents the center point of circle A) along the radius to the
outer edge (at point x and y), indicating the necessary
mathematically measurable relationship of r
and
𝞹.
.
When the metric radius of an object equals 0, r
=
0, the object may be considered infinite. So when r
=
0 it is a real singularity in certain coordinate systems.22
Obviously, having a radius means there is a fixed center (with
general coordinates of h and k) and an outer edge of the shape of
something. If all the radii are equidistant, the shape is a circle.23
The diameter, ⌀,
of that circle x 3.14… (lower case pi, 𝞹)
= the circumference of the circle, c. Inductively, c ÷ 𝞹
= ⌀,
which is 2 x r.
All finite entities project outwardly from their center point
(⊙A
represents the center point of circle A) along the radius to the
outer edge (at point x and y), indicating the necessary
mathematically measurable relationship of r
and
𝞹.
A
game is a form of activity created by a purposed intellect with a
beginning and end bounded by set rules in finite time and space where
skill is algorithmically employed with freewill by the finite
participant(s) to achieve their desired outcome. The game begins
with the participant(s) activity is as a measurable radius pushing
toward the outer part of a bounded circle. At the game’s
termination the circle is fixed determining the outcome within the
circle, as in the mental challenge of a chess match ending with x
number of moves in y time. Physical games are opiates of the stupid
where the muscle memory of the cerebellum is preferred by the
participant(s) over use of the thinking parts of the brain,
especially the frontal lobe with executive decision-making. Long
term unresolved outcome, or open-ended, games are common to academic
hypotheses. For example, named for Ernst Öpik and Jan Oort and
unproven by models, the Öpik–Oort cloud is a theoretical cloud of
predominantly icy planetesimals confidently (meaning with-faith)
proposed to surround the Sun at distances ranging from 2,000
to 200,000 astronomical units24
(0.03 to 3.2 light-years).
Finite
human ability, r, must always be less than infinite capability, so r
<
 .
Human compliance with the infinite Creator’s standards is not
possible with human efforts. A redemptive status with the Creator
can only be achieved by fatally flawed humans with faith alone (sola
fide),
as the Bible teaches.
.
Human compliance with the infinite Creator’s standards is not
possible with human efforts. A redemptive status with the Creator
can only be achieved by fatally flawed humans with faith alone (sola
fide),
as the Bible teaches.
All
children reach an age of moral awareness to choose to want what
someone else has (coveting),25
take what they want (stealing),26
and fail to be truthful (lying)27
etc.28
where they are no longer eternally innocent and their algorithm needs
to be bifurcated, β, with Divine intercession. They may reject it
and stay unredeemed,
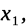 or accept God’s eternal redemption and singularity,
or accept God’s eternal redemption and singularity,
 ,
and have a new algorithm. The algorithm for the unredeemed may be
expressed as
,
and have a new algorithm. The algorithm for the unredeemed may be
expressed as
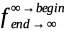 (
(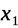 )
and the algorithm for the redeemed may be expressed as
)
and the algorithm for the redeemed may be expressed as
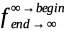 (
( ).
).
Narrow
is the way to life of bifurcation from the original sin and few find
the singularity.29
Since r
<
 , God’s Holy Spirit, ∏,30
must draw them to redemption.31
Bifurcation is first in the eternal soul’s (Greek psuchê)
algorithm, r
< 0, which was created at conception.32
Then it influences the material neuron (Greek sôma)
algorithm, r
>
0. Bifurcation of the sinner on the cross’s algorithm with
theanthropos Jesus33
began with his soul’s recognition of Jesus as Christ and his
neurons confession of Jesus as Christ.34
Immediately, Jesus indicated the sinner was redeemed.35
In that very moment he was pulled into the singularity of eternal
salvation by the Holy Spirit.36
He was regenerated37
or monergistically born again.38
He had no ability nor time to be saved by deeds but by faith alone.39
He was saved by God’s gift, which by definition gifts are freely
given things not subject to purchase, of sovereign (irresistible)
grace through given faith and not self.40
He could not have created himself or have given birth to himself.41
, God’s Holy Spirit, ∏,30
must draw them to redemption.31
Bifurcation is first in the eternal soul’s (Greek psuchê)
algorithm, r
< 0, which was created at conception.32
Then it influences the material neuron (Greek sôma)
algorithm, r
>
0. Bifurcation of the sinner on the cross’s algorithm with
theanthropos Jesus33
began with his soul’s recognition of Jesus as Christ and his
neurons confession of Jesus as Christ.34
Immediately, Jesus indicated the sinner was redeemed.35
In that very moment he was pulled into the singularity of eternal
salvation by the Holy Spirit.36
He was regenerated37
or monergistically born again.38
He had no ability nor time to be saved by deeds but by faith alone.39
He was saved by God’s gift, which by definition gifts are freely
given things not subject to purchase, of sovereign (irresistible)
grace through given faith and not self.40
He could not have created himself or have given birth to himself.41
No
one can make a clean thing from an unclean thing.42
God revealed His healing is by faith alone when the Israeli’s just
needed to look at the image on the pole and be healed (c. 1235 B.C.)
or not and suffer death.43
As was the human Isaiah,44
Jesus’ neurons were anointed by the Holy Spirit45
to preach and heal.46
Jesus stated on numerous occasions that the people’s faith of
those He healed had made them whole.47
As the image on the pole must be looked at for healing, Jesus the
Christ must be looked at, sui
generis,
for healing and redemption or not and suffer the eternal
consequences.48
In fact, God said He only answers prayer made in faith.49
No
person’s material neurons has the power to retain their nonmaterial
soul and not die.50
Everyone observes that no one takes their corruptible silver and
gold with them after death.51
Everyone that trusts in silver and gold is as deaf and blind as
those minerals.52
The term redemption itself connotes the fundament idea of being
redeemed, from an old state at a bifurcation point of the time (t)
and space λ, and redeemed to a new state, within that singularity.
Eternally, ∞ t,
that requires being bought with an eternal price,53
as with Christ’s holy complete sacrifice alone.54
Corruptible things can not be eternally added to the binary decision
to accept redemption (1) or not accept redemption (0).
All
human algorithms have innate decision-making coupling structures
(twin primes from the corpus of the monads in systematic theology’s
treebank55),
--∇--,56
for the chosen authority for good/truth and evil/untruth, justice/sin
and grace/redemption, eternity/time and infinite/space, love/life and
hate/death etc. In all literature, the written objects act and
interact within the same parameters, as with the same contrasting
notes of musical composition algorithms or the same contrasting
values in mathematical equations and chemical formulations. Humans
finitely create and recreate within the same parameters within
infinity.57
Even when the neurological coupling algorithm is compromised by a
destructive process associated with rationality, decision-making
remains within the same possible parameters, like when the wheel
coming off a moving car it predictably swerves, possibly into a
ditch, and does not disappear or take flight etc. When
Nebuchadnezzar’s neurons were bio-hacked by God, he behaved as a
predictable beast in the field for seven years.58
All
myths can be seen as containing, to some degree, the --∇--
structure of those truth elements. According to myth in Chinese
literature of the P’an-Ku
(Pan
Gu,
the Chinese god of creation),
at the beginning of time, the universe had the shape of an egg. When
the egg
broke,
a giant,
P’an-Ku,
came out of it along with two basic elements: Yin
and Yang.
Humans were believed to have been created from fleas and lice on the
P’an-Ku. The sieve of demonstrative truth can be made with the
differential calculus of rational and historical analysis. For
example, the coupling of primes shows, with good/truth and
evil/untruth, that good is connected to truth (p (good) --∇--
p (truth)) and evil is connected to untruth (p (evil) --∇--
p (untruth)), and they are connected to each other (p (good + truth)
--∇--
p (evil + untruth)). This means that there is a universal standard
of good, in the Platonic sense such as it is an immutable truth to
not do evil and murder etc., and beyond that is the reality of people
having freewill to make individual choices of good, in the
Aristotelian sense such as deciding to take one job over another. We
see from this connectedness of the treebank that neither the Platonic
nor Aristotelian models accurately excluded each other from the true
definition of good. It is also apparent that unconnectedness allows
for the fallacy of argument, such as the extreme position of Plato
for only a universal good and the position of Aristotle for only
relative good. Even the prime number of 5 alone can be seen to offer
less analytical data than when coupled with its twin of 3 and/or 7,
i.e. 3, 5 and 5, 7 twin primes.
J.R.R.
Tolkien wrote about the philosophy of myth in his novel, Tree
and Leaf,
and his poem, Mythopoeia.59
Mythological accounts surrounding death, such as with Zeus etc.,
acknowledge a chosen eternal singularity. In 2020, the photo below
of pomegranate seeds and red carnations by Carmen Hunter titled Étude
d'Hadès et de Perséphone
(French for Study of Hades and Persephone) was selected for display
at Francis Marion University’s University Place Gallery in
Florence, South Carolina. The pomegranate seeds symbolize those that
fictitiously enticed (bio-hacked) Persephone (mythological daughter
of Zeus and Demeter, and wife of Hades) to leave earth for Hades as
explained in Hesiod's
Theogony
(c.
700 B.C.) and later in the Homeric
Hymn to Demeter.
The red carnations symbolize the reality of life and death.

Finite
works are as filthy menstrual rags, r
<
0, when compared to God’s infinite holy standard60
and can not account for sins of omission.61
To sow to finite flesh reaps corruption, r
( )
< 0, and to sow to the infinite Spirit reaps eternal life, r
(
)
< 0, and to sow to the infinite Spirit reaps eternal life, r
( + ∏) > 0 →
∞ t.62
It is as foolish as the tower of failed, ⤵,
Babel attempt to reach into infinity and grab or hack,
+ ∏) > 0 →
∞ t.62
It is as foolish as the tower of failed, ⤵,
Babel attempt to reach into infinity and grab or hack,
 ,
God’s holiness and save one’s self.63
To not confess that Jesus is Christ is anti-Christ.64
Unredeemed people,
,
God’s holiness and save one’s self.63
To not confess that Jesus is Christ is anti-Christ.64
Unredeemed people,
 ,
of works hate the redeemed people65
of grace,
,
of works hate the redeemed people65
of grace,
 .66
For example, the Diet of Worms was a ruse to murder67
Martin Luther for his pointing out the filthy works of people that
thought they could reach into heaven and become righteous.
.66
For example, the Diet of Worms was a ruse to murder67
Martin Luther for his pointing out the filthy works of people that
thought they could reach into heaven and become righteous.
The
Abbaye Saint-Pierre de Solesmes, France, website explains how their
Benedictine monks, apparently not knowing God, are searching for
Him.68
Scriptures clearly indicate if a person searches for God, with all
their heart, they will find Him.69
On judgment day70
people of works will have to explain to the infinite Elohim,71
with their prideful God complex,72
how they made themselves infinitely holy, like a thief.73
A God complex is a personality choice in finite beings, especially
those with perceived great power, who desire or consider themselves
to be omniscient and omnipotent, treating others as underlings. This
desire neurologically filters all sensory input for creating the
soul’s goals and provides the subsequent motivation for all
decision-making and behavior. If this approach to life is not
reinforced it may be sublimated and manifested in an indirect manner.
A rich young ruler, ,
encountered Jesus confessing he lived a perfect life. Jesus
immediately identified the young man’s fatal fault in trusting in
his temporal wealth. Jesus said it was easier for a camel to go
through the eye of a needle than for such a person to enter God’s
heaven or become
,
encountered Jesus confessing he lived a perfect life. Jesus
immediately identified the young man’s fatal fault in trusting in
his temporal wealth. Jesus said it was easier for a camel to go
through the eye of a needle than for such a person to enter God’s
heaven or become
 .74
Beings with a God complex indicate their intentional
interchangeability or conjugation, †,
on some level, with creator God.75
An idolatrous God†
complex obviously has eternal consequences and is more of a
theological term than a psychological term.
.74
Beings with a God complex indicate their intentional
interchangeability or conjugation, †,
on some level, with creator God.75
An idolatrous God†
complex obviously has eternal consequences and is more of a
theological term than a psychological term.
Some
people at judgment will arrogantly claim (idiotic pride that
finiteness ≥
infiniteness) to have prophesied in God’s name and have cast out
devils, but He said He will tell them He never knew them.76
As with the example of Erwin Schrödinger’s cat, they can delude
themselves that they are redeemed until that day when their life’s
algorithm exposes the fact that they are eternally unredeemed. The
eternal remedy for guilt is unmerited grace. After physical death,
the eternal algorithm can not, ¬, be bifurcated,77
∞ +
 ∴
¬ β.
∴
¬ β.
Divine
works come from infinite God. The redeemed must be drawn to them as
was Moses78
and John.79
Righteous works are supernatural. After redemption, sanctification
(Greek hagiasmós
meaning
growing in holiness) is the work of the infinite Holy Spirit, r
=
∏.80
Athanasius’ Letters
to Serapion
explained the divinity of the Holy Spirit. The redeemed are to be
delivered from finite works, which are unfruitful,81
and are to walk in the Spirit showing the fruit of His infinite
power.82
They are to be witnesses of God’s extended grace, and praise Him
in words and deeds to the world.83
That is the joy and purpose for life’s strength.84
The
Holy Spirit inputs, or hacks,
 ,
by permission,85
the willing soul’s eternal algorithm so it might input the temporal
neuron algorithm.86
He hacks the algorithm, ∏
,
by permission,85
the willing soul’s eternal algorithm so it might input the temporal
neuron algorithm.86
He hacks the algorithm, ∏
 ,
with joy,87
gifts,88
power,89
comfort,90
guidance,91
truth,92
and discernment93
etc. As the redeemed are infinitely forgiven their infinite
trespasses against holy God, they are to, with Holy Spirit strength,
infinitely forgive the finite trespasses of other people against
them.94
Forgiveness is the logic of redemption. The purpose of the
transformed life is to glorify God now and in eternity.95
,
with joy,87
gifts,88
power,89
comfort,90
guidance,91
truth,92
and discernment93
etc. As the redeemed are infinitely forgiven their infinite
trespasses against holy God, they are to, with Holy Spirit strength,
infinitely forgive the finite trespasses of other people against
them.94
Forgiveness is the logic of redemption. The purpose of the
transformed life is to glorify God now and in eternity.95
The
Holy Spirit is the potential infinite radius for the redeemed’s
works. On the day of judgment, every redeemed person’s works will
be revealed by fire and if the works survive will be rewarded
accordingly because the Spirit was within them,96
r
( + ∏) > 0 →
∞ t.
+ ∏) > 0 →
∞ t.
With
infinite knowledge, the Holy Spirit hacks the redeemed, e.g. Samson,
 ,
and Mary,
,
and Mary,
 ,97
etc. Samson (b. 1090 B.C.) demonstrated that being hacked by the
Holy Spirit (c. 1065-1045 B.C.)98
is not always immediately discernible from not being hacked (c. 1045
B.C.).99
The Holy Spirit also successfully hacks the unredeemed’s
algorithm, ∏
,97
etc. Samson (b. 1090 B.C.) demonstrated that being hacked by the
Holy Spirit (c. 1065-1045 B.C.)98
is not always immediately discernible from not being hacked (c. 1045
B.C.).99
The Holy Spirit also successfully hacks the unredeemed’s
algorithm, ∏
 ⤴,
to do His will, such as Pharaoh (c. 1275 B.C.),100
pagan kings (servant of God Nebuchadnezzar c. 605-562 B.C.101
and anointed by God Cyrus, c. 538 B.C.102),
and generally convicting unrighteousness103
individuals and societies etc. The algorithms of individuals combine
to form a societal algorithm.104
God uses one societal algorithm to effect the algorithm of another
society (e.g. c. 1234 B.C. Israel,
⤴,
to do His will, such as Pharaoh (c. 1275 B.C.),100
pagan kings (servant of God Nebuchadnezzar c. 605-562 B.C.101
and anointed by God Cyrus, c. 538 B.C.102),
and generally convicting unrighteousness103
individuals and societies etc. The algorithms of individuals combine
to form a societal algorithm.104
God uses one societal algorithm to effect the algorithm of another
society (e.g. c. 1234 B.C. Israel,
 ,
to
effect Jericho,
,
to
effect Jericho,
 ,105
c. 622 B.C. Chaldea,
,105
c. 622 B.C. Chaldea,
 ,
prophesied to effect Judah, and later Assyria,
,
prophesied to effect Judah, and later Assyria,
 ,
to effect Israel106
whose majority of individuals had algorithms that turned from
,
to effect Israel106
whose majority of individuals had algorithms that turned from
 to
to
 ,
107
etc. Assyria did not specifically intend to attack Israel but God
used them for judgment and in turn they were also judged by God for
the attack,108
r
< 0). Bio-hacking is the process of attaining enough data on an
entity to understand their beliefs and motivations sufficient to
manipulate their environment to cause predicted behavioral outcomes
and seemingly lessen freewill.
,
107
etc. Assyria did not specifically intend to attack Israel but God
used them for judgment and in turn they were also judged by God for
the attack,108
r
< 0). Bio-hacking is the process of attaining enough data on an
entity to understand their beliefs and motivations sufficient to
manipulate their environment to cause predicted behavioral outcomes
and seemingly lessen freewill.
Elect
sinless, by grace, angels109
are organized under an archangel who is under omnipotent creator
Christ.110
Angels blinded the homosexual men of Sodom,
 ,
who were trying to gang rape them (c. 1896 B.C.).111
Since expelled from heaven,112
fallen angels or demons, under the created Satan,113
temporarily battle angels114
and saints,
,
who were trying to gang rape them (c. 1896 B.C.).111
Since expelled from heaven,112
fallen angels or demons, under the created Satan,113
temporarily battle angels114
and saints,
 ,115
and ultimately lose.116
Eph. 6:12 indicates there are four areas of demon responsibility and
hacking. First, principalities
or rulers
are
not found doing Satan’s evil among ordinary people. They are
likely specifically chosen by Satan to rule in the heavenly places
over all the other demons. They also have the special work of
hacking earthly rulers117
and governments. Second, powers
are the demons that spread the power of evil and darkness into any
given area of people’s lives. They have been described as the evil
force that hacks feelings and imaginations, enticing people to commit
horrific sinful crimes, possessing the unredeemed118
etc. Third, the
rulers of the darkness of this age
or the
world forces of this darkness is
the group identified as the demons that fight truth with spiritual
blindness using superstitions, witchcraft, ignorance, stupidity,
pride etc. Last, wicked
spirits in heavenly places
or the
spiritual forces of wickedness in the heavenly places
are the counterintelligence demons who join the church and profess
holiness. They identify and attack the most religious people with
heresies, such as salvation by works, spiritualism, Darwinism and
other forms of God†
complexes.
,115
and ultimately lose.116
Eph. 6:12 indicates there are four areas of demon responsibility and
hacking. First, principalities
or rulers
are
not found doing Satan’s evil among ordinary people. They are
likely specifically chosen by Satan to rule in the heavenly places
over all the other demons. They also have the special work of
hacking earthly rulers117
and governments. Second, powers
are the demons that spread the power of evil and darkness into any
given area of people’s lives. They have been described as the evil
force that hacks feelings and imaginations, enticing people to commit
horrific sinful crimes, possessing the unredeemed118
etc. Third, the
rulers of the darkness of this age
or the
world forces of this darkness is
the group identified as the demons that fight truth with spiritual
blindness using superstitions, witchcraft, ignorance, stupidity,
pride etc. Last, wicked
spirits in heavenly places
or the
spiritual forces of wickedness in the heavenly places
are the counterintelligence demons who join the church and profess
holiness. They identify and attack the most religious people with
heresies, such as salvation by works, spiritualism, Darwinism and
other forms of God†
complexes.
God
knew Satan would choose to become prideful119
and that his pioneering God†
complex algorithm could be used to improve the algorithms of the
redeemed, such as with Job. Satan’s
first corruptly bio-hacked Eve’s neuron algorithm. He saw she
desired the forbidden fruit and inputted her algorithm with the lie
that she could become a god and she succumbed making the hack a
success, ⤴,
(c. 3940 B.C.). Adam was not deceived but committed the original sin
by also eating the forbidden fruit.120
King David,
 ,
wanted
to manage the Israeli people better and was successfully, ⤴,
hacked to number them in a census (c. 973 B.C.).121
David did not trust God’s provisions and safety, and by giving the
people a number also wrongly indicated all people have equal value
and are not uniquely gifted by God for His purpose. Justly, there
was a harsh penalty for the sin.122
,
wanted
to manage the Israeli people better and was successfully, ⤴,
hacked to number them in a census (c. 973 B.C.).121
David did not trust God’s provisions and safety, and by giving the
people a number also wrongly indicated all people have equal value
and are not uniquely gifted by God for His purpose. Justly, there
was a harsh penalty for the sin.122
Addressing
Satan’s īnfāmāta
toward Job,
 ,
God
famously gave Satan permission to take Job’s family, wealth, and
health in an attempt manipulate Job to curse God. As God knew, the
hack failed, ⤵,
because Job had sufficient theological knowledge to use the
experience to correct a flaw in his algorithm before being fully
restored.123
In the fall of 27 A.D., Jesus fasted.124
Satan used Jesus’ hunger to try and hack Him to wrongly get His
food,125
knowing God’s security Satan tried to get Jesus to wrongly test
that reality,126
and knowing Jesus role as the world leader Satan tried to get Jesus
to wrongly attain that status.127
They all failed, ⤵,
because Jesus had perfect knowledge of the Scriptures—the manual
for human algorithms.128
,
God
famously gave Satan permission to take Job’s family, wealth, and
health in an attempt manipulate Job to curse God. As God knew, the
hack failed, ⤵,
because Job had sufficient theological knowledge to use the
experience to correct a flaw in his algorithm before being fully
restored.123
In the fall of 27 A.D., Jesus fasted.124
Satan used Jesus’ hunger to try and hack Him to wrongly get His
food,125
knowing God’s security Satan tried to get Jesus to wrongly test
that reality,126
and knowing Jesus role as the world leader Satan tried to get Jesus
to wrongly attain that status.127
They all failed, ⤵,
because Jesus had perfect knowledge of the Scriptures—the manual
for human algorithms.128
Satan
wanted to sift Peter,
 ,129
a future leader of the Christianity. When confronted with fear,
Peter lied by denying he knew Jesus and cursed.130
He wept bitterly131
after realizing he had been successfully hacked. He briefly returned
to his former life.132
Then he confessed love for Jesus and accepted his commission to feed
Jesus’ sheep.133
He did so until he was murdered. As God knew would happen, Peter
grew from fear to courage,134
from pride to humility,135
from ignorance to knowledge,136
from rebellion to submission,137
from focus on self to focus on Christ.138
John the Baptist,
,129
a future leader of the Christianity. When confronted with fear,
Peter lied by denying he knew Jesus and cursed.130
He wept bitterly131
after realizing he had been successfully hacked. He briefly returned
to his former life.132
Then he confessed love for Jesus and accepted his commission to feed
Jesus’ sheep.133
He did so until he was murdered. As God knew would happen, Peter
grew from fear to courage,134
from pride to humility,135
from ignorance to knowledge,136
from rebellion to submission,137
from focus on self to focus on Christ.138
John the Baptist,
 ,
said God must increase and he must decrease.139
Jesus perfectly modeled the ultimate human will is to do God’s
perfect will.140
,
said God must increase and he must decrease.139
Jesus perfectly modeled the ultimate human will is to do God’s
perfect will.140
Redeemed
parents, ,
are to hack their children with Scriptural teaching141
and correction.142
The redeemed are to also hack the idolatrous unredeemed143
with the gospel.144
Short of physical violence145
and being murdered,146
they should expect to either be mocked,147
be asked questions,148
or witness redemption belief149
before ending the interaction.150
,
are to hack their children with Scriptural teaching141
and correction.142
The redeemed are to also hack the idolatrous unredeemed143
with the gospel.144
Short of physical violence145
and being murdered,146
they should expect to either be mocked,147
be asked questions,148
or witness redemption belief149
before ending the interaction.150
The
redeemed are as God-focused sheep among unredeemed self-focused
wolves.151
When hypocrites (know truth and do not do it = once removed from
truth) bio-hack a proselyte (know the hypocrite example of truth and
do not do it = 2 x removed from truth) they make them 2 x as likely
for eternally damnation in hell as the hypocrites themselves.152
Unredeemed human attempts at bio-hacking other human unredeemed and
redeemed is expected. In captivity (c. 597 B.C.), Daniel’s,
 ,
(meaning [Yahweh] God is my Judge) name was changed by his Babylonian
captors,
,
(meaning [Yahweh] God is my Judge) name was changed by his Babylonian
captors,
 ,
to Belteshazzar (meaning [the Babylonian god] Bel will protect),
along with Hananiah,
,
to Belteshazzar (meaning [the Babylonian god] Bel will protect),
along with Hananiah,
 ,
(Yahweh is gracious) to Shadrach (inspiration of the sun), Mishael,
,
(Yahweh is gracious) to Shadrach (inspiration of the sun), Mishael,
 ,
(Yahweh is without equal) to Meshach (belongs to the goddess of
wine), and Azariah,
,
(Yahweh is without equal) to Meshach (belongs to the goddess of
wine), and Azariah,
 ,
(Yahweh is my helper) to Abednego (servant of Nego).153
,
(Yahweh is my helper) to Abednego (servant of Nego).153
The
redeemed are not to think their fiery trials are strange.154
Nehemiah,
 ,
was given the mission by God to rebuild Jerusalem and God’s
enemies,
,
was given the mission by God to rebuild Jerusalem and God’s
enemies,
 ,
predictably resisted his efforts (c. 445 B.C.). He was mocked155
but his prayer defeated the hack,156
the threat of violence toward him157
was defeated by prayer and diligent security,158
fear159
was defeated by security and remembering God and continuing work,160
distractions161
were ignored,162
lies163
were call lies and prayer continued,164
death threats165
were defeated by prayer and discerning that evil,166
,
predictably resisted his efforts (c. 445 B.C.). He was mocked155
but his prayer defeated the hack,156
the threat of violence toward him157
was defeated by prayer and diligent security,158
fear159
was defeated by security and remembering God and continuing work,160
distractions161
were ignored,162
lies163
were call lies and prayer continued,164
death threats165
were defeated by prayer and discerning that evil,166

 ⤵.
Similarly, U.S. President Donald Trump and Israeli Prime Minister
Benjamin Netanyahu have a righteous mission to protect and rebuild
their nations. Especially in 2019,167
they have each been met with the exact opposition techniques by
people that are also known enemies of God,
⤵.
Similarly, U.S. President Donald Trump and Israeli Prime Minister
Benjamin Netanyahu have a righteous mission to protect and rebuild
their nations. Especially in 2019,167
they have each been met with the exact opposition techniques by
people that are also known enemies of God,
 .
In his 1983 Templeton Prize address for Progress in Religion,
Aleksandr Solzhenitsyn, a Christian and 1970 Nobel Prize winner for
Literature, stated that evil Russian policies were due to the people
forgetting God.168
.
In his 1983 Templeton Prize address for Progress in Religion,
Aleksandr Solzhenitsyn, a Christian and 1970 Nobel Prize winner for
Literature, stated that evil Russian policies were due to the people
forgetting God.168
Meditation
is a means of one’s soul hacking its own neurological algorithm.
Zen
(Buddhist) meditation
or Zazen (za
meaning sitting, and Zen
meaning meditation
in Japanese),
is a proposed way of self-discovery. It is Ch'an
in Chinese and originally called Dhyana (Sanskrit) in India. Its
practitioners have God†
complexes and corruptly teach all human beings have God’s nature or
the Buddha-nature with the potential to attain enlightenment, within
them, but God’s nature has been clouded by ignorance. To overcome
that ignorance they reject the study of truth of scriptures in favor
of meditation expecting a sudden breakthrough of insight and
awareness of ultimate reality.169
Since they idolatrously believe themselves to be God in the making,
they confine their algorithm input to their own self with finite
potential, which negates their Divine nature which must have the
attribute of infinity with pre-self-existence to their own
existence.170
They are their object of meditation, for their own satisfaction, and
timing. Conversely, biblical teaching of meditation is the quiet
contemplation of spiritual truths. The object is God’s words,171
His instruction,172
and law173
for understanding,174
spiritual satisfaction,175
and knowledge176
to be conducted all day177
and at evening.178
The redeemed’s faith179,
 ,
requires hope,180
which allows for their neurological algorithm to have needed rest.181
,
requires hope,180
which allows for their neurological algorithm to have needed rest.181
Recent
studies show certain species of pine, birch, oak etc. give off
different phytoncides. They are airborne chemicals that plants give
off to protect themselves from insects. Phytoncides have
antibacterial and antifungal qualities which help plants fight
disease. When people breathe in these chemicals, the body responds by
increasing the number and activity of a type of white blood cell
called natural killer cells (NK). These cells kill tumor and virus
infected cells in human bodies. In one study, increased NK activity
from a 3-day and 2-night forest trip lasted for more than 30 days.
We know that the mere physical activity of walking has many
beneficial health benefits. It is also known that breathing in fresh
oxygen rich air in a tranquil forest is good for health. Now it is
understood that there may be other advantages to walking in the
woods. Shinto and Buddhist meditation style adherents have given
this scientifically true activity the name of shinrin-yoku
(Japanese for forest-bath). Forest bathing is actually no more of a
true religious experience with the redemptive God than walking on a
tread mill, having oxygen therapy, and getting a penicillin shot at a
doctor’s office,182
r
- ∏ = 0 ∴
¬ β =
 .
.
Enhanced
artificial intelligence collaboration of assets is expected for
future bio-hacking. The communist Chinese military company Huawei’s
CEO, Ren Zhengfei, and Israeli professor and historian Yuval
Noah Harari
spoke in Davos,
Switzerland, January 2020,
about the future of technologies and the rise of digital
surveillance. Harari
warned companies
and governments can essentially hack
humans. The communist Zhengfei said he believes in the face of new
technologies, and that humanity will be able to use them
beneficially. Most people aspire to a good life, not a miserable
life, he seductively concluded. The old philosophy of communism is
for a few self-appointed elites with God†
complexes, like Zhengfei and others, to essentially hack and enslave
all other people with demonic deception and violence. The name,
communism, itself demonstrates adverse inference on the human
algorithm to efficiently achieve the hierarchy of needs.183
Chinese born and raised to the age of 25, Yu Meng, now a U.S.
citizen, has been made the Chief Investment Officer of CalPERS
(California Public Employees Retirement System) which supports gun
control of U.S. law abiding citizens and supports companies that
supply the Chinese military. When Meng worked for a Chinese
investment fund, he was recruited by the Thousand Talents Initiative.
That is a known Chinese intelligence program. In keeping with
chapter 2, stratagem 4 of the Thirty-Six
Stratagems
(hide a knife behind a smile), it is designed to charm Western
businessmen, scientists, and other experts to secretly contribute to
communist China. The explicit goal is to obtain superior Western
technology and research for China's enslavement of the free world,184
r
< 0. A psalmist might righteously denounce these unrepentant
perpetrators of wickedness, and seek their punishment praying that
their teeth be broken off185
and that their children be fatherless.186
The deist U.S. founding father, Thomas
Jefferson
wrote "I have sworn upon the altar
of God eternal
hostility against every form of tyranny
over the mind
of man."187
In
the prophesied future, people that have rejected the God of the
Bible,
 ,
and say they want peace and food will have their fears and anger
hacked by the beastly new world leader who promises to meet their
desires. They will fatally accept his mark of eternal rebellion
against God.188
Anti-Christs will obtain their finite kingdom with flatteries, r <
0, to corrupt their unredeemed followers but people with belief in
God will survive using the tools of God outlined in Scripture.189
The atoms of a supersolid begin to coalesce when close to absolute
zero and act as a superfluid, which flows with zero viscosity. In
such a conducive state for humans, Christ types love God with all
their hearts, souls and minds and their neighbor as their selves,
they grow in favor with God and with rational man, glorify God,
humbly serve others, are self-sacrificing, prayerfully search
Scriptures, are truthful, care for children and the innocent, are
diligent, comply with God’s plan for sexuality, and support God’s
geopolitical state of Israel, etc. Conversely, anti-Christ types do
not love God nor their neighbors, grow away from favor with God and
rational man, glorify themselves, pridefully have others serve them,
sacrifice others, oppose Scriptures, are liars, murder children and
others, are slothful, promote sexual perversion, and oppose God’s
prophesied plan for the nation-state of Israel, etc.
,
and say they want peace and food will have their fears and anger
hacked by the beastly new world leader who promises to meet their
desires. They will fatally accept his mark of eternal rebellion
against God.188
Anti-Christs will obtain their finite kingdom with flatteries, r <
0, to corrupt their unredeemed followers but people with belief in
God will survive using the tools of God outlined in Scripture.189
The atoms of a supersolid begin to coalesce when close to absolute
zero and act as a superfluid, which flows with zero viscosity. In
such a conducive state for humans, Christ types love God with all
their hearts, souls and minds and their neighbor as their selves,
they grow in favor with God and with rational man, glorify God,
humbly serve others, are self-sacrificing, prayerfully search
Scriptures, are truthful, care for children and the innocent, are
diligent, comply with God’s plan for sexuality, and support God’s
geopolitical state of Israel, etc. Conversely, anti-Christ types do
not love God nor their neighbors, grow away from favor with God and
rational man, glorify themselves, pridefully have others serve them,
sacrifice others, oppose Scriptures, are liars, murder children and
others, are slothful, promote sexual perversion, and oppose God’s
prophesied plan for the nation-state of Israel, etc.
God
bio-hacked plants190
( e.g.
gourd,191
fig tree192
etc.), insects193
(
e.g.
gourd,191
fig tree192
etc.), insects193
( ,
e.g.
lice,194
flies,195
locusts,196
insect larva grub or worm197
etc.) and animals (
,
e.g.
lice,194
flies,195
locusts,196
insect larva grub or worm197
etc.) and animals (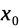 ,
e.g. ark,198
ram,199
frogs,200
animals,201
first-born,202
quails,203
ravens,204
bears,205
lions,206
whale207
etc.),
,
e.g. ark,198
ram,199
frogs,200
animals,201
first-born,202
quails,203
ravens,204
bears,205
lions,206
whale207
etc.),
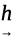
 ⤴.
With God’s permission, demons bio-hacked swine,208
⤴.
With God’s permission, demons bio-hacked swine,208

 ⤴.
Humans are expected by God to successfully bio-hack the temporal
algorithms,
⤴.
Humans are expected by God to successfully bio-hack the temporal
algorithms,
 209
of plants210
and animals,211
209
of plants210
and animals,211

 ⤴.
Jesus said the righteous could bio-hack fig trees as He did.212
A 2020 poll of 2,000
U.S. millennials
(25-39 year olds) discovered 67% believe taking care of house plants
is too much of a challenge. Almost half don’t currently own plants
because they don’t know how to take care of them, and 20% find the
pressure of taking care of a plant is greater than having a root
canal,213
(see endnote 40). (See U.S. college students confessing to potted
plants in 2019 at https://systematicpoliticalscience.com/plants.html)
⤴.
Jesus said the righteous could bio-hack fig trees as He did.212
A 2020 poll of 2,000
U.S. millennials
(25-39 year olds) discovered 67% believe taking care of house plants
is too much of a challenge. Almost half don’t currently own plants
because they don’t know how to take care of them, and 20% find the
pressure of taking care of a plant is greater than having a root
canal,213
(see endnote 40). (See U.S. college students confessing to potted
plants in 2019 at https://systematicpoliticalscience.com/plants.html)
Environmental
injustice occurs when the Creator’s design is violated. The
righteous are expected to regard the life of their animals.214
Three times Balaam,

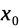 ⤵,
unsuccessfully inputted violence into his donkey’s algorithm,
⤵,
unsuccessfully inputted violence into his donkey’s algorithm,
 ,
to manipulate its obedience. The donkey was given the ability by God
to rebuke him for that trespass. The donkey had saved Balaam’s
life from Divine judgment. Balaam repented for the sin of doing his
own will (c. 1235 B.C.).215
,
to manipulate its obedience. The donkey was given the ability by God
to rebuke him for that trespass. The donkey had saved Balaam’s
life from Divine judgment. Balaam repented for the sin of doing his
own will (c. 1235 B.C.).215
From
worms to dogs etc., the mortality rates of life increase
exponentially and form a straight time line from birth to death.
Human life expectancy is around seventy-five years.216
After the age of thirty, the likelihood of human death217
doubles every 8½ years (see the Gompertz–Makeham
law).218
Men do not know their end and are as fish caught in a net.219
Humans are increasingly interested in trying to bio-hack the
cellular algorithm of the human machine to increase longevity or at
least increase the quality of life until death.220
Bacterial
life, ,
was bio-hacked by washing clothes in (alcoholic) wine (c. 1689 B.C.)221
and in water, as well as vessel’s and human bodies (c. 1275 B.C.).222
Today, humans justly kill bacteria inconsistent with their desires
using skin surface rubs and mouth rinse (alcohol), hand wipes and
soaps (quaternary ammonium compounds) etc. Germicidal activity of
alcohols increase with increased chain length of carbons (maximum of
five to eight), and when used with water (i.e. 70% alcohol is more
active than 95% alcohol). The most used are ethanol and isopropanol
with follow up skin treatments of iodophor. The germicidal activity
of quaternary ammonium compounds is determined by the organic groups,
especially having eight to eighteen carbon long groups. They include
benzalkonium chloride and cetylpyridinium chloride.223
,
was bio-hacked by washing clothes in (alcoholic) wine (c. 1689 B.C.)221
and in water, as well as vessel’s and human bodies (c. 1275 B.C.).222
Today, humans justly kill bacteria inconsistent with their desires
using skin surface rubs and mouth rinse (alcohol), hand wipes and
soaps (quaternary ammonium compounds) etc. Germicidal activity of
alcohols increase with increased chain length of carbons (maximum of
five to eight), and when used with water (i.e. 70% alcohol is more
active than 95% alcohol). The most used are ethanol and isopropanol
with follow up skin treatments of iodophor. The germicidal activity
of quaternary ammonium compounds is determined by the organic groups,
especially having eight to eighteen carbon long groups. They include
benzalkonium chloride and cetylpyridinium chloride.223
In
2019, it was noted that monoclonal antibodies (mAbs) represent an
important platform for the development of biotherapeutic products.
Most mAbs are produced in mammalian cells, but several mAbs are made
in Escherichia
coli,
including therapeutic fragments.224
By this process, it can be seen that bio-hacking basic cellular
structure(s) model the bio-hacking of more complex biological
entities, especially with closed loop systems, θ. In 2020, the
paper Estimating
the Asymptomatic Proportion of 2019 Novel Coronavirus onboard the
Princess Cruises Ship statistically
modeled the ratio of non-asymptomatic v symptomatic of COVID-19, the
Chinese Corona-Virus (see a summary of the COVID-19 timeline225).
Observations were treated as survival data with right censoring or
point censoring.226
The probability of being asymptomatic along with the infection time
of each individual was estimated in a Bayesian framework using the
Hamiltonian Monte Carlo algorithm.227
(For a detailed description of the model used and the computation see
the Technical Appendix.)228
In March 2020, the University of Tennessee Oak Ridge National
Laboratory Center for Molecular Biophysics used an algorithm to model
COVID-19 disease outcomes. Saving months of efforts, their world’s
most powerful supercomputer (Summit) was able to quickly narrow
research from thousands of likely dead ends to a few possibilities
that might warrant further study. To slow the virus from spreading,
political leaders ordered people to stay at home in accordance with
the advice of medical advisors. This caused stress from loss of
income, increased domestic violence, increase in burglaries,
increased suicides, and increased drug use etc. Some political
leaders,
 ,
used this situation as an opportunity to shut down churches, control
sectors of the economy, promote the murder of babies, promote
marijuana use, promote the purchase of lottery tickets by the poor,
and release convicted criminals from prison who predictively
immediately reoffended.229
In March 2020, it was reported that the U.S. Defense Advanced
Research Projects Agency (DARPA) and the tech company Profusa are
developing an injectable biosensor to detect pandemic infections and
are recommending all people have the under-the-skin injection.230
U.S. President Trump joined the Southern Baptist Convention in
calling for a National Day of Prayer on Sunday 15 March, 2020, for
the issues, such as COVID-19, that are plaguing the nation. He said,
“We are a country that, throughout our history, has looked to God
for protection and strength in times like these.”
,
used this situation as an opportunity to shut down churches, control
sectors of the economy, promote the murder of babies, promote
marijuana use, promote the purchase of lottery tickets by the poor,
and release convicted criminals from prison who predictively
immediately reoffended.229
In March 2020, it was reported that the U.S. Defense Advanced
Research Projects Agency (DARPA) and the tech company Profusa are
developing an injectable biosensor to detect pandemic infections and
are recommending all people have the under-the-skin injection.230
U.S. President Trump joined the Southern Baptist Convention in
calling for a National Day of Prayer on Sunday 15 March, 2020, for
the issues, such as COVID-19, that are plaguing the nation. He said,
“We are a country that, throughout our history, has looked to God
for protection and strength in times like these.”
Corona
is Latin for crown, as worn by a monarch. In the span of a few
weeks, the crown of the world’s idols, such as sports and
entertainment, money, bar and restaurant scenes etc. were removed by
the virus, as is God’s just historical hacking pattern of merciful
judgment (predictive analytics, if a
then b…),231
along with daily anti-Christ government indoctrination of children in
schools. Christian churches were forced to expand their luke-warm
ritualistic methods of worship with technology to reach the world.
“And this gospel of the kingdom shall be preached in the whole
world for a testimony unto all the nations; and then shall the end
come.”232
A
reasoning algorithm for finite intellects, both
 and
and
 ,
to hack themselves and potentially others is the scientific method.
This systematic pursuit of knowledge, from the known to the unknown,
begins with the recognition of a phenomena. Next, a hypothesis is
made regarding the data collected about the phenomena. Then, an
attempt(s) is made to replicate the phenomena, which either proves
the hypothesis or disproves the hypothesis. If the hypothesis is
proven it may be used and disseminated to other people for use. If
it is disproven, step two, collecting data and making a hypothesis,
is repeated by
,
to hack themselves and potentially others is the scientific method.
This systematic pursuit of knowledge, from the known to the unknown,
begins with the recognition of a phenomena. Next, a hypothesis is
made regarding the data collected about the phenomena. Then, an
attempt(s) is made to replicate the phenomena, which either proves
the hypothesis or disproves the hypothesis. If the hypothesis is
proven it may be used and disseminated to other people for use. If
it is disproven, step two, collecting data and making a hypothesis,
is repeated by
 until
a hypothesis is proven. If the result is contrary to the desires of
until
a hypothesis is proven. If the result is contrary to the desires of
 ,
they may elect to ignore the outcome and promote their desired
outcome, i.e. intelligent life on other planets, evolution, no sola
Scriptura
or sola
fide
etc.
,
they may elect to ignore the outcome and promote their desired
outcome, i.e. intelligent life on other planets, evolution, no sola
Scriptura
or sola
fide
etc.
This
survey of human algorithms have shown them to be deterministic.
Meaning the system of rules determines what the possible outcomes
can/will be. Unpredictability and uncertainty of outcomes are due to
the ignorance of finite analysis and are ultimately not
chaotic—deterministic system(s) ≠ chaos.233
Deterministic human algorithms ⇌
deterministic universe system ⇌
determiner Creator ⇌
pre-existent
first Causer of all effects ⇌
infinite God—Yahweh. The Determiner would know the outcome of His
deterministic algorithm(s). Therefore, infinite God always has had
complete knowledge data and created finite man has incomplete
knowledge data but has the ability to observe the general symmetry of
the complete knowledge data possessed of God by accepting that
reality by faith. To not accept that reality requires contriving the
irrational notion of chaos,
 ,234
in a deterministic system to fill the void of understanding. For
example, the COVID-19 timeline (endnote 225) may be seen as having a
beginning point and a future end point, as with algorithms. Since it
is an algorithm, it can not be the result of true chaos and would be
deterministic,
,234
in a deterministic system to fill the void of understanding. For
example, the COVID-19 timeline (endnote 225) may be seen as having a
beginning point and a future end point, as with algorithms. Since it
is an algorithm, it can not be the result of true chaos and would be
deterministic,
 (
(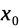 )
∴
¬ †
)
∴
¬ †
 .
Since it is deterministic, there must have been a finite determiner,
secondary to the infinite primary Determiner of all things (Yahweh),
for the event observer to identify by who gained at its end state.
As with God’s lovingly testing of humans for their spiritual
growth, humans purposely test their created software systems in
production in order to build user confidence in the system's
capability to withstand turbulent and unexpected conditions to build
resilience against network, infrastructure, and application failures
called chaos engineering. Deterministic algorithms naturally
weaponize mathematics.
.
Since it is deterministic, there must have been a finite determiner,
secondary to the infinite primary Determiner of all things (Yahweh),
for the event observer to identify by who gained at its end state.
As with God’s lovingly testing of humans for their spiritual
growth, humans purposely test their created software systems in
production in order to build user confidence in the system's
capability to withstand turbulent and unexpected conditions to build
resilience against network, infrastructure, and application failures
called chaos engineering. Deterministic algorithms naturally
weaponize mathematics.
Additionally,
the mathematics of the redemptive singularity and other bifurcation
points were lightly touched on for a foundation of more advanced
study of its natural weaponization against the defeated temporal
spirit of untruth and for the victorious eternal Holy Spirit of
truth, Π
(John 14:17). Being bio-hacked and attempting to bio-hack should be
a recognized reality of the algorithms for all intelligent finite
life and points to the urgent need for humans to accept the
redemptive tools contained in Scriptures. Except the Lord build the
house, the builder’s labor in vain.235
Catholic Yugoslav 1961 Nobel Prize winner for literature, Ivo
Andrić
noted in his 1945 novel, Na
Drini ćuprija
(The
Bridge On The Drina),
“…all of us die
only once, whereas great
men die twice,
once when they leave this world and a second
time
when their lifework
disappears,”
r
= 0. Great men are not always wise.236
Jesus said he that is greatest among you shall be your servant.237
Blessed are those that die in the Lord, they rest in their labors
and their works eternally follow them,238
r
> 0. The rooster has crowed…239
a massa’.
HOSANNA!
If
I justify myself, my own mouth shall condemn me.
Job 9:20
1
See his Pensées.
C. S. Lewis indicated in his The
Great Divorce that
there are only two kinds
of people in the end:
those who say to God, Thy will be done, and those to whom God says,
in the end, Thy will be done. All that are in Hell, choose it.
Without that self-choice there could be no Hell. No soul that
seriously and constantly desires joy will ever miss it.
2
Nicomachus of Gerasa's
Introduction to
Arithmetic describes
the sieve and attributes it to Eratosthenes of Cyrene (c. 276-195
B.C.).
3
Twin primes are prime numbers
with a gap of 2 numbers, such as the twin prime pairs of 3 and 5, 5
and 7, 41 and 43 or 659 and 661 etc. They are not to be confused
with co-primes, which are numbers that have no common factor except
1, such as 8 and 9 or 15 and 32.
4
The latter includes 9/3 star
polygons and the palindromagon, the construction of which sequences
the six possible permutations of 3, 6, 9: 639→693→963←369←396←936.
5
This observation is from a
computer programmer’s email exchange with Dallas F. Bell, Jr.
during January, 2020.
6
https://xlinux.nist.gov/dads/HTML/deterministicAlgorithm.html
7
https://xlinux.nist.gov/dads/HTML/nondetermAlgo.html
8
Edgar Eaves et al. Introductory
to Mathematical Analysis
(5th
Ed.), Allyn and Bacon Inc., 1978, p. 268.
9
See his 2004 work Algorithmic
Mathematics.
http://www.maths.qmul.ac.uk/~lsoicher/ambook.pdf
10
Vivaldi was recommended to
Dallas F. Bell Jr. during an email exchange with Eduard Babulak,
professor of computer science at Liberty University, during January,
2020.
https://systematicpoliticalscience.com/physics.html
13
Stephen Kleene’s (2013)
Mathematical Logic,
Dover Publishing Inc., pp. 223-233, 241-241.
14
A scalar
is an element of a field which is used to define a vector space. A
quantity described by multiple scalars, such as having both
direction and magnitude, is called a vector.
16
The battle for the supreme
authority of God’s immutable Scripture over man’s corrupting
input, no matter how well meaning the original motivation is still r
< 0, has always
been waged. In the Jewish arena for example, Karaites
(meaning readers) were Jews who accepted the authority of the Torah
but not that of the Talmudic rabbis who interpreted traditions and
legislated the religious practices of the majority of Jews. The
Karaites correctly pointed to the Torah’s own strictures against
additions or diminishments: “You shall not add to that which I
command you and you shall not subtract from it, to keep the
commandments of the Lord your God” (Deuteronomy 4:2). The Psalmist
writes, in 19:8, “The Torah of the Lord is perfect.” Rabbi’s,
such as Saadya ben Joseph (aka Saadya Gaon) etc., argued that the
Torah is not self-explanatory. Thus, it commands Jews not to perform
m’lakhah
(work) on the Sabbath but does not define exactly what m’lakhah
is. They add that even Karaite authorities agree that certain
things, like prayer, are commanded by God, yet prayer itself is not
explicitly commanded in the Torah. And even for commandments that
are specifically ordained, like the commandment to wear fringes on
one’s garments, no instructions are given as to the proper kind of
fringes or how they are to be created. Today, this movement against
God’s infinite words as fallible is led by Catholic doctrine to
heretically promote, r
< 0, their finite leadership as infallible (Vatican I, 1870,
constitution Pastor
aeternus, Kenneth
Himes’ 2005 Modern
Catholic Social Teaching,
Georgetown University Press, pp. 114, 133). They falsely argue
Scripture
never says that Scripture
is the sole infallible authority for God’s Word meaning, as they
are prosecuted worldwide for raping little boys, r
< 0, they consider themselves more infallible than all others
before them. They indicate Scripture
mandates the use of tradition and that alone
disproves sola
Scriptura, which
justifies their heretical filling of the vacuum of needed Divine
authority, r <
0. The Scriptures say they are all inspired by the Holy Spirit (II
Tim. 3:16; II Peter 1:21). To subtract from them or add to them
(Deut. 4:2; Rev. 22:18-19) is to call the Holy Spirit a liar and is
blasphemy against the Holy Spirit, which will/can not be eternally
forgiven (Luke 12:10).
17
General Lee
by Fitzhugh Lee and his nephew, D. Appleton & Co., New York,
1895, p. 417.
18
Robert E. Lee The Christian
by William J. Johnson, Mott Media, Milford MI, 1976.
19
The Soul of Lee
by Randolph H. McKim, Longmans, Green & Co., New York, 1918, p.
217.
20
Marse Robert, Knight
of the Confederacy by
James C. Young, Rae D. Henkle Inc., New York, 1929, p. 344.
21
The Boolean expression gives
rise to a bifurcation point, β,
in the execution of the algorithm (Greek small letter beta).
22
See Arnab Choudhuri’s book
Astrophysics for
Physicists (2015),
Cambridge University Press, pp. 405-407.
23
The earth was biblically
described as a circle (c. 545-538 B.C., Is. 40:22). The number of
pi, lower case, is theorized to be infinite. If so, it is also
theorized that if the numbers were converted to letters all words
would be spelled out at some point in its sequence. Words
communicate ideas. This indicates that all knowledge has always
existed in infinity prior to human existence.
24
Astronomical units are roughly
the distance from Earth to the Sun and equal to about 150 million
kilometers or 93 million miles.
29
Matt. 7:14; Rom. 5:12-21.
30
Holy Spirit (II Sam.23:2; Mark
12:36), represented by
the upper case pi.
https://systematicpoliticalscience.com/philosophiae.html
32
Job 10:11; Ps. 139:13-16; Is.
44:24.
33
In the scriptures, Jesus
refers to “my soul.”
(Matthew 26:38) Then
saith he unto them, My soul
is exceeding sorrowful,
even unto death: tarry ye here, and watch with me. (Mark 14:34) And
saith unto them, My soul
is exceeding sorrowful
unto death: tarry ye here, and watch. (John 12:27) Now is my soul
troubled; and what shall
I say? Father, save me from this hour: but for this cause came I
unto this hour.
37
Greek palingenesia
meaning to become again, Matt. 19:28; Titus 3:5. See the entry for
regeneration in Alton Bryant’s The
New Compact Bible Dictionary,
Zondervan Publishing House (1973, tenth printing), pp. 493-494.
See the new
creature section at
https://systematicpoliticalscience.com/bacteriology.html
40
Eph. 2:8. Once a person has
asked omniscient, and thus sovereign, God for redemption, He
omnipotently bestows grace for the insurmountable unrighteousness of
that person, which is not resistible and is accepted by given faith.
This process can be compared to the root canal process. When a
person sees a dentist to take care of the pain and infection of a
bad tooth that inflames the gums to the heart, he sits in the chair
and the dentist administers gas (nitrous oxide, N2O),
drills off the decayed tooth, removes the infected material, flushes
the area with topical bacteria killing ozone (trioxygen, O3),
secretes a base material to rebuild the tooth, and cures it with a
laser. That new tooth will keep out future bacteria. Taking the
follow-up prescription for antibiotics will aid in fighting off the
residue infection. Having a root canal means a better life and
should not be feared but should be embraced (see page 10).
Obviously, redemption means a better eternal life and should be
embraced.
(https://www.ncbi.nlm.nih.gov/pmc/articles/PMC4243235/
Regarding a
clinical ozone generator
for dental
applications. Not only does ozone
kill all the bad
bacteria, fungi, viruses
and protozoans, it also removes their breakdown products as well as
other necrotic debris. In the case of caries, much of the waste is
highly acidic. [Dental
caries is a bacterially
mediated disease characterized by demineralization of the tooth
surface, which may lead
to cavitation, discomfort, pain and eventual tooth loss.] That's
what contributes to the initial attack on enamel. Its free radical
negative charge on the oxygen
is drawn deeply into the tooth, toward any positively charged
[acidic] bacteria,
such as the anaerobic
bacteria found in tooth
decay. The ozone
sterilized dental surface
can be quickly [around one hour] remineralized by the calcium
phosphate present in saliva, thus becoming hard and resistant to
further bacterial attack
for at least three months.)
46
Luke 4:18-19; Acts 10:38.
47
Matt. 9:22; Mark 5:34, 10:52;
Luke 7:50, 8:48; 17:19, 18:42.
51
Eccl. 2:18-19, 5:15; Luke
12:15-21.
54
I Peter 1:20; II Peter 2:1.
55
A non-exhaustive treebank list
of monads is at
https://SystematicPoliticalScience.com/monads.html
56
Represents a mechanical
interlock between two devises.
59
http://home.agh.edu.pl/~evermind/jrrtolkien/mythopoeia.htm
62
Hosea 10:12; Rom. 8:13; Gal.
6:8.
66
Acts 15:11; Rom. 3:24.
67
Ex. 20:13; Matt. 5:21-22.
68
“The Abbey of Saint-Pierre de
Solesmes is steeped in 1,000 years of history and is a leading
centre for Gregorian chant. Above all, however, it is a living
community of Benedictine monks searching for God. Since our
monastery is a place of silence and recollection, we invite you to
share in our spirituality…” https://www.solesmes.com/
Chanting
focuses on the body and is a form of self-worship (Amos 6:3-6).
69
Deut. 4:29; II Chron. 15:4; Is.
55:6-7: Jere. 29:13; Acts 17:27.
72
A God†
Complex is not a clinical term but is often related to Narcissistic
Personality Disorder which is characterized by the Diagnostic and
Statistical Manual of Mental Disorders (published by the American
Psychiatric Association)
as a pervasive
pattern of grandiosity, need for admiration, and a lack of empathy.
Ernest Jones’
description was in his Essays
in Applied Psycho-Analysis.
75
In functional analysis, each bounded linear operator on a complex
Hilbert space has a corresponding Hermitian
adjoint or operator
named after Charles Hermite.
For example, the adjoint of an operator A
may also be called the Hermitian
conjugate or transpose
of A
denoted by A†.
Adjoints of operators generalize conjugate transposes of square
matrices to (possibly) infinite-dimensional situations. An operator
is said to be Hermitian if A†
= A.
Hermite was a practicing Catholic who was influenced by the
Christian beliefs of Augustin-Louis Cauchy and others.
80
Gal. 3:3; Phil.
2:12-13.I Peter 1:2. See the entry for sanctification in Alton
Bryant’s The New
Compact Bible Dictionary,
Zondervan Publishing House (1973, tenth printing), p. 522.
81
Eph. 5:11; II Tim. 4:18.
82
Rom. 8:1-4; Gal. 5:16-18.
83
Matt. 24:14; Luke 18:43; Heb.
13:15.
85
Hacking has been narrowly
defined as a person(s) using a computer(s) to nefariously operate
another person’s computer(s).
https://cyber.harvard.edu/wg_home/uploads/356/ComputerHacking.pdf
A wider
definition is the act of an entity intended to effect another
entity(s) either for a malevolent purpose or for a benevolent
purpose.
93
I Cor. 2:10-16; I John 4:1-6.
94
Matt. 18:35; Eph. 4:32.
96
Eccl. 12:14; I Cor. 3:13-16.
97
Matt. 1:20; Luke 1:35.
98
Judges 13:24-25, 15:14.
101
Jere. 25:9, 27:6, 43:10.
104
https://systematicpoliticalscience.com/awakenings.html
110
Is. 6:2-3; I Thess. 4:16.
112
Is. 14:12-14; Jude 6.
114
Dan. 10:13, 20; Rev. 12:7-9.
117
God allows evil spirits to hack
government leaders, such as recorded in Judges 9:23, I Sam.
16:14-23.
118
Matt. 8:28-29, 9:32-33,
12:22-23, 15:22-28, 17:14-21; Mark 1:23-26, 5:2-10, 16:19; Luke
8:27-31, 11:24-26 etc.
119
Is. 14:12-15; John 12:31. Pride
makes beings lower and honor lifts the humble (Prov. 29:23).
121
II Sam. 24:1-4; I Chron. 21:1-6.
122
II Sam. 24:12-14; I Chron.
21:10-13.
131
Matt. 26:75; Mark 14:72; Luke 22:62.
133
John 21:15-19; Acts; I and II Peter.
134
Matt. 14:28-31; 26:58.
141
Deut. 4:9, 6:6-7; Prov. 22:6.
142
Deut. 21:18-21; Prov. 22:15,
23:13. These teachings recognize human innate negativity bias,
which means negative reinforcement is many times more of an
effective behavioral modifier than positive reinforcement.
151
Matt. 10:16; Luke 10:3; Titus
3:3. Recent examples of self-focused wolves are people that
publically confess to groups of strangers how many sins they have
committed against God without any sense of fear and trembling and
others that want to publically discuss sexual intimacy in marriage.
Neither of those examples are biblically modeled nor can be shown to
focus on God’s glory. False teachers are expected to attempt to
bio-hack (Rev. 2:14, 20) and murder God’s redeemed, as with
Antipas (Rev. 2:13).
153
Dan. 1:7. This is an example of
how righteous people, Daniel etc., are caught up in God’s
righteous judgment of the overall unrighteous society.
167
Trump and Netanyahu were each
formally accused of wrong doing.
168
https://www.nationalreview.com/2018/12/aleksandr-solzhenitsyn-men-have-forgotten-god-speech/
169
See the entry for Zen in the
2004 Encyclopedia
Britannica (premium
service).
170
See the comparative religion
section at https://systematicpoliticalscience.com/synthesis.html
182
https://www.ncbi.nlm.nih.gov/pmc/articles/PMC2793341/
183
https://systematicpoliticalscience.com/mapping.html
187
This quote is from a letter to
the Christian U.S. founding father Dr. Benjamin Rush - Monticello,
Sep. 23, 1800. It appears under the dome of the Jefferson
Memorial in Washington,
DC.
188
Rev. 13:14-18. The unredeemed
are primarily motivated by fear, especially of God’s impending
judgment, and anger toward the reality of God’s law. This makes
them easily hacked and is a chosen state unequipped to have a life
harmonious to God’s creation and law. The wicked flee when no one
pursues them (Judges 7:13-22; II Kings 7:5-7 etc.) but the righteous
are bold as a lion (Prov.28:1).
189
Dan. 11:21-32. If possible,
false Christ’s would bio-hack God’s redeemed elect (Mark 13:22).
190
https://systematicpoliticalscience.com/plants.html
Of course,
although all non-human biological life seem to have temporal
algorithms, the categories have different levels of created
sophistication to accomplish their designed purpose, such as
animals, insects, plants, and bacteria etc. For example, honey bees
use the sun as a directional marker when leaving and returning to
the hive. The returning foragers do dances to tell the others
location, distance, and direction to the nectar. Karl von Frisch won
a Nobel Peace Prize in 1973 for his work on honey bee
communications.
https://askabiologist.asu.edu/bee-dance-game/introduction.html
Even the non-biological stars sing in harmonious tones together (Job
38:7).
https://exoplanets.nasa.gov/news/1516/symphony-of-stars-the-science-of-stellar-sound-waves/
If God
desired, stones would cry out (Josh. 24:27; Hab. 2:11; Luke 19:40)
or raise up children to Abraham (Matt. 3:9).
193
https://systematicpoliticalscience.com/bacteriology.html
197
Jonah 4:7. Unrepentant and so underdeveloped people,
 ,
are associated with worms
(Job 25:6; Ps. 22:6; Is. 66:24; Mark 10:44, 48).
,
are associated with worms
(Job 25:6; Ps. 22:6; Is. 66:24; Mark 10:44, 48).
209
There are no references to
animals in the prophesied New Jerusalem (Rev.).
210
This is common in horticulture
and especially in cross-breeding.
213
https://nypost.com/2020/01/24/millennials-say-being-a-plant-parent-is-harder-than-they-expected/
215
Num. 22:21-34; II Peter 2:15-16.
217
https://www.cdc.gov/nchs/data/nvsr/nvsr54/nvsr54_14.pdf
218
Named for Benjamin Gompertz and
William Makeham, the Gompertz–Makeham
law states that the human
death rate is the sum of an age-dependent component, which increases
exponentially with age, and an age-independent component.
220
See the recent works of Robert Hariri, M.D. and Ph.D. awarded the
2018 Pontifical Key Innovation Award by the Vatican's
Pontifical Council for Culture and the Cura Foundation, at Human
Longevity Inc. and Cynthia Kenyon, Ph.D. and Darwinian evolutionist,
at Calico etc.
222
Lev. 11:25, 13:6, 15:2-13 etc.
223
Patrick Murray’s et al. 2016
Medical Microbiology
(8th
ed.), Elsevier Inc., pp. 12-14.
224
https://www.jbc.org/content/294/48/18046
225
2015: The U.S. NIH
(National Institutes of
Health) is known to have
funded, $3.7 million, the bat coronavirus research (SARS-CoV) that
will be unleashed on the world by the Chinese Wuhan Institute of
Virology lab’s likely “gain-of-function” research (a Chinese
bio-warfare lab; under atheistic communism all undertakings are part
of a warfare strategy to dominate others, their raison
d’être).
https://www.dailymail.co.uk/news/article-8211291/U-S-government-gave-3-7million-grant-Wuhan-lab-experimented-coronavirus-source-bats.html
2016: U.S
presidential candidate Trump declares to put an end to the decades
of American policy of loss in trade deals with China.
2017: China
installs a puppet director general Tedros
Adhanom
Ghebreyesus,
to the World Health Organization (WHO), who specializes in malaria
(in accordance with the Chinese Thirty-Six Stratagems* chapt. 1
strat. 3, kill with a borrowed knife.)
Early 2018:
the U.S. State Department warned of the unsafe research practices by
the Chinese Wuhan lab.
Early 2019:
a female Chinese intelligence agent is arrested at Trump’s
Mar-a-Lago resort with computer virus software and spy devices
(*chapt. 6 strat. 1, the honeypot.)
2019: Plans
are made by U.S. tourists and others for the largest human migration
on earth to China to celebrate chunyun
(Lunar New Year
Spring Festival, 10 Jan.-18 Feb 2020), (*chap. 1 strat. 5, loot a
burning house).
Mid-2019:
Supported by democracy and justice loving Americans, Hong Kong
Christians riot in opposition to a Chinese communist criminal
extradition bill that targets Hong Kong advocates of democracy.
Nov. 2019:
Hidden by Chinese officials, the first case of COVID-19 is reported
to have occurred in Wuhan China (*chap. 6 strat. 4, inflict injury
on oneself), the location of their covert bio-warfare lab.
End-2019:
U.S. finalizes a trade deal with China, which will cost China nearly
a trillion dollars in tariffs.
Jan. 2020:
A Chinese medical doctor, Li Wenliang, tells the world about
COVID-19 and the communist government arrests him.
End Jan.
2020: Trump restricts travel from China into the U.S. The World
Health Organization and U.S. media call his prudent acts racist.
Feb. 2020:
Dr. Li Wenliang, the Chinese whistleblower, dies.
8 Mar.
2020: It is revealed that (Brazilian) dinner guests of Trump at
Mar-a-Lago test positive for COVID-19.
Mar. 2020:
A Chinese foreign ministry official releases a false report that the
U.S. military started COVID-19 (*chapt. 6 strat. 5, use chain
stratagems and chapt. 2 strat. 1, make up a lie). The tech company
Twitter does not remove the false allegation.
Mar. 2020:
Tedros
Adhanom
Ghebreyesus,
the WHO director
general and malaria expert, supports China’s false COVID-19
statistics as does the U.S. media.
Mar. 2020:
A California doctor, and others, say they are seeing significant
success in prescribing the malaria
drug hydroxychloroquine, touted by Republican Trump and mocked by
U.S. democrats and media, in combination with zinc to treat patients
with severe symptoms
of COVID-19.
(Countries with malaria have virtually no COVID-19 cases and
vice-versa.)
April 2020:
U.S. states are using Chinese made drones to illegally collect data
on its law abiding citizens, as modeled by the Chinese government.
End April
2020: Over 180 countries have COVID-19 cases with their
self-reporting ranging from fairly accurate to very inaccurate, as
with China. The U.S. accurately reports having more than the
average cases. Approximately 20% of Americans have lost their jobs
(30 million).
(Note:
The Chinese
word for "crisis"
is (simplified Chinese) 危机;
(traditional Chinese) 危機;
(pinyin) wēijī
(Mainland),
wéijī (Taiwan).
In the
Xinhua
Zidian
(in Chinese) (10th revised, large-print ed. Beijing: Commercial
Press. 2004. p. 205) translation
of the character 机/機
(jī)
has multiple meanings: a point where things happen, change. e.g. 生机,
危机,
转机.
Derivation1. an event that has a confidential nature which can lead
to success or failure. e.g. 军机,
机密,
机要.
Derivation2. chance (opportunity), good timing. e.g. 随机应变,
勿失良机,
好时机
Future:
If II Chron. 7:13-14 (see endnote 231) is not achieved, then more
societal consequences will justly follow. Depending on how people
perceive their situation, lower need levels will be a reality. If a
sufficient number of people perceive dropping to the survival level
then revolution or reformation will follow (force projection
multipliers are concentrations of demographic subsets, i.e. racial
identity or religious identity etc., and geographic region identity
etc.). If it is perceived dropping only to the economic security
level then severe societal competition will follow. The predictive
analytics technique of logical regression may be employed to look at
data points of the binary variables.
https://systematicpoliticalscience.com/precursors.html
226
In statistics, censoring is a condition in which the value of a
measurement or observation is only partially known. Left
censoring is when a data
point is below a certain value but it is unknown by how much.
Interval censoring
is when a data point is somewhere on an interval between two values.
Right censoring
is when a data point is above a certain value but it is unknown by
how much. Right
censoring (aka point
censoring)
happens when the subject leaves the study before it is finished
(loss of a follow-up) or when the event of interest does not happen
during the course of the study (end of the study). Placebos are
known to affect dropout rates
because they do not offer relief from symptoms. The problem of
data-driven models and validation is that you need data to use
it; under uncertain and changing conditions where data just
isn't available, the model outputs are nonsense. The classic type 3
error. If you can't change parameters from what you validated
before, your (closed loop system) model has no use—garbage →
in (θi) = garbage →
out (θo). As the
financial times recently reported on the UK’s silly use of viral
pneumonia models for COVID-19 at
https://www.ft.com/content/249daf9a-67c3-11ea-800d-da70cff6e4d3
227
In computational physics and
statistics, the Hamiltonian
Monte Carlo algorithm
(aka hybrid Monte Carlo),
is a Markov
chain Monte Carlo
method for obtaining a sequence of random samples which converge to
being distributed according to a target probability distribution for
which direct sampling is difficult.
228
https://doi.org/10.1101/2020.02.20.20025866
https://www.medrxiv.org/content/10.1101/2020.02.20.20025866v2
Worldwide
demographic statistics show different corona-virus rates. Although
virtually economically equal, U.S. blacks have around 4 times the
rate of Orientals or Caucasians. Blacks are also many times more
likely to have heart disease, diabetes, asthma, staphylococcus
infections due to unhealthy sanitary habits, and AIDS/HIV etc. They
have much higher infant death rates and all have sickle cell anemia.
Ultra-Orthodox Jews in Israel (12%) have a much higher rate of
cases in Israel (70%) than the rest of the population, but this is
due their intentionally not complying with the advice of their
adversarial government leaders.
229
https://www.dailymail.co.uk/news/article-8188041/Ministers-accused-treating-Doomsday-scientist-like-demigod.html
230
Rev. 14:9. Prophecy of end
times notes an increase in loimos
(Greek for
pestilences, plagues, pandemics, disease [allowed by God]: Matt.
24:7; Luke 21:11).
231
II Chron. 7:13-14. (See the Future section of endnote 225.)
233
In 2005, Heinz Georg Schuster wrote an introduction book on
deterministic chaos.
234
The Talmud (Chagigah
12a) addresses the Old Testament concept of tohu
(tohuw;
Gen. 1:2, without form; I Sam. 12:21 and Is. 45:18-19, vain; Job
6:18, nothing, and Job 26:7, empty places; Is. 24:10, confusion, and
Is. 29:21 and 49:4, nought). The New Testament also addresses
confusion (I Cor. 14:33; James 3:16) and a state of disorderliness
(II Thess. 3:7). Each of those biblical descriptions have, on some
level, been loosely associated with the idea of chaos. Greek
mythology actually promoted the oxymoron principle of chaos
as the origin of everything and the very first thing that ever
existed. Occultists also hold to this belief, as their necessary
false alternative to Creator God. For example, the homosexual
Satanist Edward Crowley (aka Aleister Crowley the wickedest man in
the world) used the chaos symbol of an eight-pointed star with
arrows pointing outward, as do those in role-playing games. In an
email exchange with Dallas F. Bell Jr. in April, 2020, Robert
Bishop, professor of physics and science at Wheaton College,
indicated that different scientists use different symbols defining
their meaning of chaos, which prevents an accepted symbol for chaos
in formulae. https://plato.stanford.edu/entries/chaos/ God
is omnipotent, omnipresent, and omniscient and the Holy Spirit, Π,
exhibiting the ratio of the diameter of all things to the
circumference of all knowledge of all things, prevents the
possibility of true chaos. This reality could be represented by a
square, actual Divine guiding rules for an observation, with a c,
finite perceived chaos, inside,
 .
.
236
Job 32:9; I Cor. 1:26.
239
Massa’ (Hebrew
for burden, prophecy, tribute, doom, song). Matt. 26:74-75. In
Christianity, the rooster symbolizes a sinner's acceptance of divine
pardon through Jesus Christ. Many Protestant and Catholic churches
in Europe have a rooster on top of their steeples, such as the
Daviot Parish Church in Scotland. It is common to see carved
roosters on the top of wooden churches in Norway. Most of the
older churches in the Netherlands have weather vanes that are golden
roosters. The golden rooster is said to be a symbol of Jesus
Christ who breaks the power of the darkness, brings forgiveness of
sins, and announces a new day by the power of His resurrection.
Some churches use the rooster as their logo, such as a church in
Manhattan. The rooster appears in the catacombs of Rome.
A 3rd-century fresco of Jesus Christ was found in
the Catacomb of Callixtus, which portrays Jesus as the Good
Shepherd with a rooster at his feet. Two red roosters appear with a
cross over the center of the arch in the Christian "Tomb
of the Cocks" in Beit Jibrin, 13 miles northwest
of Hebron. The association of the rooster with light could
explain why some clay oil lamps had rooster images, such as an oil
lamp with a rooster was found in North Africa dating to the
3rd-century
A.D. The Christianized Khasi people
(an indigenous
ethnic group of Meghalaya in north-eastern India) believe the
sacrifice of a rooster is a substitute for man, because they believe
that the cock when sacrificed "bears the sins of the man."
In Judaism, the Hebrew word gever
means both "man" and "rooster" so punishment of
the rooster can be substituted for that of a person who deserves
punishment. Kapparot is practiced by some Jews shortly before Yom
Kippur (the Day of Atonement). First, selections from Isaiah 11:9,
Psalms 107:10, 14, and 17-21, and Job 33:23-24 are recited; then a
rooster (for a male) or a hen (for a female) is held above the
person's head and swung in a circle three times, while the following
is spoken: "This is my exchange, my substitute, my atonement;
this rooster (or hen) shall go to its death, but I shall go to a
good, long life, and to peace." "Cock's
crow"
is a technical term in Jewish law (kri'at
hagever (קריאת
הגבר)).
It is a time of day prior to dawn that marks the end of night. In
the Yoruba,
descendants from a
variety of West African communities, creation story the rooster
serves the Creator by scratching out the dirt to form the dry land.
The rooster might be seen as a Christ-like symbol since Christians
believe that all things were made through Christ. At Sun shrines in
Japan, roosters freely roam the grounds. The rooster is the tenth
creature in the Chinese zodiac. They believe there is a rooster in
the sun. When a white rooster is place on a coffin, it is believed
that it will keep demons at bay. See Wolfram Eberhard’s (1996) A
Dictionary of Chinese Symbols,
Routledge, London, pp. 68-69.

